The world has gone remote. But our intense and sudden use of video conferencing to communicate isn’t the big technology news lately. It’s Zoombombing, where hackers sneak into video conferencing sessions then disrupt it with pornographic images and hate speech. It’s gotten everyone’s attention—including the FBI. Here’s what you need to know about Zoombombing.
Zoombombing is Bad Technology News
Most business leadership would agree that Zoombombing is potentially less harmful than, say, ransomware, but it certainly isn’t the kind of innovation in technology news that we appreciate. Especially now, when video conferencing is so vital to keeping collaboration alive during the COVID-19 crisis.
Zoombombing is when trolls search the internet for links to videoconferences held on the popular platform Zoom. They take advantage of a loophole default setting (some would call this a user error) that allows them to enter a videoconference and hijack it, usually to post offensive images or verbal abuse. Zoom’s default setting allows any meeting participant to share their screen without permission from the event host. If the host fails to disable this setting, they may be Zoombombed. Links to Zoom videoconferences are frequently shared now on social media platforms and webpages; it’s a great way to bring people together. But these virtual visits are easy to find and exploit.
In the last month, Zoombombers have:
- Repeatedly encroached on and disrupted Alcoholics Anonymous (AA meetings) telling participants, “Alcohol is so good.”
- Posted porn on a Chipotle video meeting with hundreds of participants
- Attacked churches in Austin, Texas during Sunday school lessons
- Infiltrated a Kalamazoo, Michigan City Commission meeting. It was their first virtual meeting.
Zoombombers have hit schools too. And, now the FBI is warning the public of these threats. The only good news during this disruption is that: a) There are other video conferencing solutions to consider, and b) There are ways to mitigate the risk with a few simple best security practices for your organizations.
Here’s how to protect your team from Zoombombers.
Business Leadership Tips—Protect Your Team from Zoombombers
The New York Times reports that Zoom has become our default videoconferencing platform. Zoom usage exploded to more than 25 million daily active users around the globe. But Zoom’s security defaults have created a lot of fun for hackers who, we should note, are also stuck at home. The FBI’s Boston’s bureau issued a five-point warning for Zoom users to protect themselves by:
- Not making meetings public. Require a meeting password or use the waiting room feature to review attendees before starting.
- Do not share a link to a videoconference in a public forum, instead send out the link to individual attendees.
- Change the screen sharing feature to “Host Only.”
- Make sure users have uploaded the most recent Zoom version; the January 2020 version has crucial security updates.
- Discuss information security with your remote teams so everyone understands the risk and how to mitigate it.
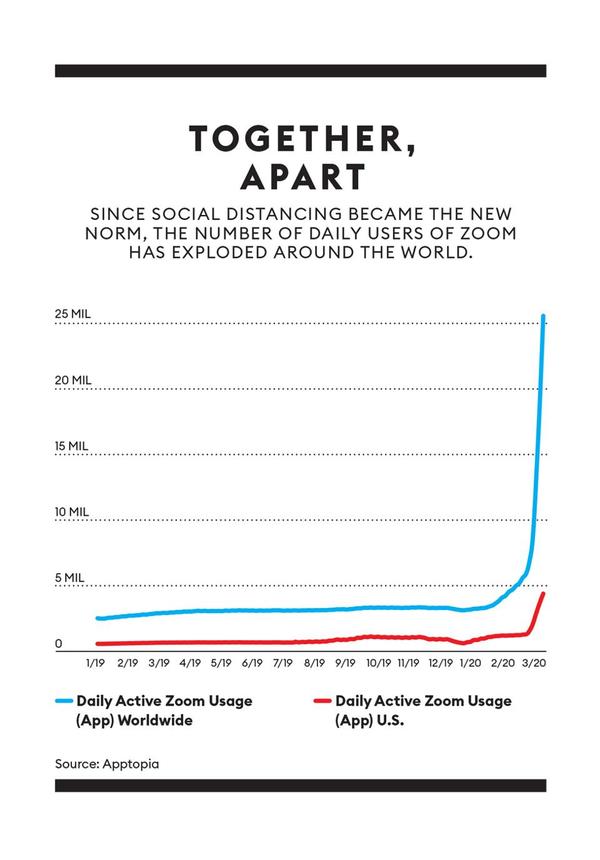
Zoom usage has skyrocketed.
Zoombombers are just the latest glitch hampering our ability to connect during a very uncertain time in our history. Business leadership can take proactive steps to make certain team communication stays secure and efficient or as long as the shutdown lasts.
